SSL Certificates Questions
SSL certificates support articles: if you have any questions about 20i's free Secure Socket Layer Certificates, this is the place to look first.
Can I use the free SSL if my site doesn't use the 20i nameservers?
Let’s Encrypt require the authoritative nameservers are set to our own to issue their Wildcard Certificates under the ACME DNS verification method - That is not something we control. There are however multiple benefits to applying a wildcard SSL to your hosting package:
- Adding new subdomains will automatically be secured under the wildcard SSL. This makes maintaining and managing your websites certificates much easier as there’s no need to worry about applying and keeping track of multiple SSLs. (e.g. we’ll provision an SSL that covers *.example.com for your domain)
- The wildcard SSL is also used to cover custom mail hostnames. If you want to use imap/smtp.yourdomain.com you can do so, just make sure the free SSL is applied to the hosting package and we’ll take care of the rest – mail will be sent and received over a secure connection.
- These SSLs renew automatically every 90-days without any intervention or action being required, you can therefore rest assured that once you’ve applied the free SSL you’ll have the best chance to getting your website loading 100% via HTTPS.
How do I activate my free SSL?
If you’re unable to point the nameservers to our own, then you can use our Simple SSL which can be purchased from within your account: https://my.20i.com/services/order-ssl
 Austin B.
Austin B.Can I point an A record to a 20i package and get the free SSL certificate?
No. To be able to apply the free SSL certificates your site(s) need to use the 20i nameservers.
This is because the SSL certificates are installed locally to the 20i platform.
 Austin B.
Austin B.Why should you use Force HTTPS on your website?
Using HTTPS instead of HTTP means that communications between your browser and a website is encrypted via the use of an SSL (Secure Socket Layer).
Even if your website doesn’t handle sensitive data, it’s a good idea to make sure your website loads securely over HTTPS. It’s now becoming a requirement for many new browser features as well as having an impact on search engine rankings.
To make sure your website loads securely, you need to make sure that it is prefixed with HTTPS instead of HTTP. This can be done in a few different ways. Outlined below are the most common ways to do this.
How to force HTTPS using our tool
- Log in to My20i and head to Manage Hosting and select Manage on the package you want to force HTTPS for.
- Select the SSL/TLS icon.
- Select Enable Force HTTPS. This will redirect website users to HTTPS. As long as the website has an SSL certificate and all content loads via HTTPS, the site should show as secure.
How do I use the .htaccess file to force HTTPS?
Another way that has the potential for more specific configuration is to use a .htaccess file rule. If you don’t have a .htaccess file, you can create one via FTP or File Manager and then add the code:
RewriteEngine On
RewriteCond %{env:HTTPS} !on
RewriteRule ^(.*)$ https://www.example.com/$1 [R,L]
If you already have a .htaccess file then make sure you don’t duplicate the line: RewriteEngine On
If after enabling force HTTPS the website shows insecure, then you’ll need to make sure that:
- You have an SSL certificate on the site
- You don’t have mixed content, more details here: mixed content.
 Austin B.
Austin B.How can I generate a Certificate Signing Request (CSR)?
When ordering an SSL certificate, you can be asked to generate a Certificate Signing Request (CSR).
This is an encoded block of text that the Certificate Authority request before issuing an SSL/TLS certificate. It contains information about the organisation, domain name and locality.
Step-by-step guide on CSR generation:
Step 1: Choose a CSR generator tool
There are many CSR generator tools available online like:
Step 2: Fill out the CSR information form
Once you've chosen a CSR generator tool, you'll be asked to fill out a form with information about your website, including:
Country – the two-letter country code of your organisation
State/province – the state or province where your organisation is located
Locality – the city where your organisation is located
Organisation – the legal name of your organisation
Organisational unit – the department or division within your organisation responsible for the website
Common name (CN) – the fully qualified domain name (FQDN) of your website (e.g. www.example.com)
Key size – you are given option of 2048-bit or 4096-bit, we recommend the 4096 as this has a higher encryption level.
Some CSR generators might also ask to provide additional information, such as your email address and the type of server software you're using.
Step 3: Generate the CSR
Once you've filled out the form, click the "Generate CSR" or "Create CSR" button. The CSR generator tool will then create a text file containing the CSR and the private key for your website.
Ensure that you keep a record of both the CSR and private key.
Step 4: Submit the CSR to a Certificate Authority (CA)
To obtain an SSL/TLS certificate for your website, you'll need to submit the CSR to a Certificate Authority (CA). The CA will use the information in the CSR to verify your website's identity and generate a digital certificate.
When submitting the CSR, you'll typically be asked to provide additional information, such as your contact information and payment details.
Step 5: Install the SSL/TLS certificate on your web server
Once you've received the digital certificate from the CA, you'll need to install it. The process for installing the certificate will depend on the web server software you're using. You can typically find instructions for installing the certificate in the documentation for your web server software.
With 20i, this is quick and easy process through our control panel. Here’s a guide on how to install a third-party SSL certificate.
 Austin B.
Austin B.Can I install a third-party SSL certificate?
Yes: if you have an existing external or third-party SSL certificate you can install this at 20i.
Your certificate provider will need to provide the following sections for us to be able to install the SSL certificate:
- Certificate
- Private Key
- CA Bundle / Intermediate Certificate
These details will need to be entered within the SSL/TLS section within a 20i hosting package: Manage Hosting -> [select package] -> SSL/TLS.

Note: Your Private Key will have been provided when you generated a CSR using your organisation's details. If you have any questions about this, the certificate provider will be able to help.
Please also note that SSL certificates can take up to 30 minutes to install on to the web server. If your A records are then pointing to the IP address of the hosting package then your site should show as secure.
If you don’t have an external SSL then you can either apply the Free 20i SSL, or purchase a 20i SSL from here.
Reseller Help - How do I support my clients?
These steps should help you provide helpful and effective support to your clients.
1) If your client has a third-party SSL it's always best to request this in the appropiate format. i.e. the individual Certificate, Private Key and Intermediate Certificate sections. It'll make installing the SSL at 20i much easier.
 Austin B.
Austin B.How do I add a Let's Encrypt certificate to my Unmanaged VPS?
Unlike our shared web hosting platforms, some manual intervention is required to enable and install Let's Encrypt certificates on a 20i Unmanaged VPS. The process of installing Let's Encrypt certificates depends on the operating system in use, and whether or not one is using a control panel, such as cPanel.
cPanel
To install a Let's Encrypt SSL on a cPanel VPS you'll need to do the following.
1). Login to the VPS via SSH.
2). Once logged in, preferably as root, or a user with sudo access, run the following command:
/scripts/install_lets_encrypt_autossl_provider
Once ran, the Let's Encrypt plugin will be installed.
Once installed, you will then be able to issue a Let's Encrypt certificate via the WHM interface. Specifically, you will need to access Home > SSL/TLS > Manage AutoSSL.
Within the Manage AutoSSL section, you will need to select Let's Encrypt from the list of available AutoSSL providers. Once selected, agree to the terms of service, and select 'Save'.
After agreeing to the terms of service, you will then be able to issue certificates for the users/domains/accounts on the VPS.
This can then be done by selecting the 'Run AutoSSL For All Users' facility, which will then subsequently attempt to issue Let's Encrypt certificates for all users. Alternatively, certificates can be issued on a user by user basis by selecting 'Manage Users' on the 'Manage AutoSSL' page.
CentOS 6
For those without a control panel, Let's Encrypt certificates can be installed through the installation and use of Certbot.
To get started, you'll need to access the VPS via SSH, as either the root user, or a user with sudo privleges.
Once you've logged into your VPS, you'll need to run the following commands:
wget https://dl.eff.org/certbot-auto
sudo mv certbot-auto /usr/local/bin/certbot-auto
sudo chown root /usr/local/bin/certbot-auto
sudo chmod 0755 /usr/local/bin/certbot-auto
You'll then need to run Certbot to grab and install your certificates. The exact command you need to run will differ depending on whether you're running an Apache setup, or an Nginx setup.
For those running an Apache setup, you will need to run the following:
sudo /usr/local/bin/certbot-auto --apache
Those running Nginx will need to run:
sudo /usr/local/bin/certbot-auto --nginx
Upon the enacting of either command, you may then be prompted to install a number of packages and dependencies. If this happens, once the list of packages and dependencies are present, simply enter 'Y' to accept and install.
Once the packages and dependencies have been installed (if you were prompted to do so), Certbot will then prompt you to enter several credentials.
Firstly, you'll be prompted to enter an email address for any urgent renewal or security notices. This can be anything you like, though we recommend ensuring it is an address you manage, and have access-to. Once you have entered the email address, press 'ENTER' on your keyboard.
Subsequently, you'll then be prompted to accept the Let's Encrypt Terms of Service, which must be accepted in order to be able to issue certificates. To accept, simply enter the letter 'A' and press 'ENTER'.
You will then be prompted to share your email address with the Electronic Frontier Foundation. Sharing your email address is up to you. To share, you will want to enter the letter 'Y', and then press 'ENTER'. Conversely, if you do not wish to share your email address, enter the letter 'N', and press 'ENTER'.
Once complete, a list of available domains will be displayed in a numbered menu. The numbered menu is generated based on the virtualhosts/domains defined in your Apache/Nginx configuration file. To install a certificate for a particular domain, you'll need to enter the number(s) you desire, and 'ENTER'.
A certificate will then be generated and installed for your chosen domain(s).
To ensure that the certificate renews automatically in the future, you may want to ensure a cronjob has been set-up to renew it automatically. This can be done by running the following command:
echo "0 0,12 * * * root python -c 'import random; import time; time.sleep(random.random() * 3600)' && /usr/local/bin/certbot-auto renew" | sudo tee -a /etc/crontab > /dev/null
CentOS 7
The setup of Certbot via CentOS/RHEL 7 is slightly different to that of CentOS 6.
Firstly, you'll want to ensure that the Extra Packages for Enterprise Linux (EPEL) repository has been enabled. To enable the EPEL repository, run the following command:
sudo yum install epel-release
Once you have enabled access to the repository, you can then run the following to install Certbot:
sudo yum install certbot python2-certbot-apache
If you are running Nginx, you will need to run the following:
sudo yum install certbot python2-certbot-nginx
Once installed, you can then look to issue a certificate for any of the domains/virtualhosts mentioned in your Apache and Nginx configuration files.
To begin the process for Apache servers, run the following:
sudo certbot --apache
For Nginx, you will need to run:
sudo certbot --nginx
Again, as with the CentOS 6 example above, you'll be prompted to enter information, i.e. an email address through which you can be contacted, whether you agree to the Let's Encrypt Terms of Service, and whether you wish to share the entered email address.
Next, you'll be prompted to enter the number of the domain/virtualhost for which you would like to install a Let's Encrypt certificate. Enter the number you desire, and then press 'ENTER' on your keyboard.
Once issued, you will then want to set-up the automatic renewal of your Let's Encrypt certificate(s) by running the following command:
echo "0 0,12 * * * root python -c 'import random; import time; time.sleep(random.random() * 3600)' && certbot renew" | sudo tee -a /etc/crontab > /dev/null
 Andrew Porter
Andrew PorterSimple SSL Purchase and Renewal Process
Here's how to purchase or renew a Simple SSL.
Buy SSL certificate:
- You can order an SSL from the control panel here: Simple SSL
- Once you've completed the order, a verification email is sent to admin@theDomain.com which needs approving. This is usually sent within 30 minutes of the order.
- Once you've approved the verification email there's nothing more you need to do. We'll install the SSL to the package within 1 hour, automatically.
- You can then view the Simple SSL by going to Manage Hosting -> Manage -> SSL/TLS
Note: You can view the process of an SSL order from here: https://my.20i.com/services/manage-ssl
Renew your SSL certificate:
- When the Simple SSL comes up for renewal an email will be sent to the admin@theDomain.com mailbox to verify the renewal.
- Once the email has been approved there's nothing more you need to do, the SSL will renew on its renewal date.
Note: You can view the process of a renewal from here: https://my.20i.com/services/manage-ssl
Reseller Hosting Help - How do I support my clients?
These steps should help you provide helpful and effective support to your clients.
1) If the client hasn't received the verification email, you can resend it from here: https://my.20i.com/services/manage-ssl
2) If the client can't set up an admin@ mailbox for the verification email, they can set up a forwarder to go from admin@ -> another mailbox, however, this is the only method to verify ownership of the domain and is set by the issuing certificate authority.
Can I export my SSL and use it elsewhere?
SSL certificates that are purchased through us can be used on other platforms – in order to obtain the files to install the certificate, you will need to raise a ticket with our Support Team with reference to the domain the SSL was purchased for and what type of file you need.
If you are unsure of the specific type of file you need, the host you’re installing the SSL on will be able to confirm this. Once this is raised as a ticket, our team will then fetch the necessary files, help convert the SSL to the format you need and then provide this to you ready to use.
 Austin B.
Austin B.How to auto-activate SSLs for websites
With this feature you, as a hosting reseller, can provide an extra service to your customers. With SSL certificates being installed automatically your customer has not to worry about this security feature for the website.
Not everyone of your hosting customers might as comfortable in navigating a control panel as you are and having this process automated might even reduce the amount of support tickets for you, as questions like ‘where do I find my free SSL certificate and ‘how to I install free SSL on my website’ are obsolete with the automated installation.
How to auto-activate SSLs for websites
Resellers can configure SSL certificates to auto-activate when a new website is created. To do this:
- Head to your Hosting Package Types - you can either create a new package type, or select Options > Edit to update an existing type.
- Locate the Security section and select Auto activate free SSL, select Save Changes.
- When a new package is created using the package type with this option enabled, we'll automatically install the free SSL.
Please note that for 20i Resellers, this option is turned on by default.
We can only install the free SSL if the nameservers of the website point to 20i. For more information please see this article: Can I use the free SSL if my site doesn’t use the 20i nameservers?
 Austin B.
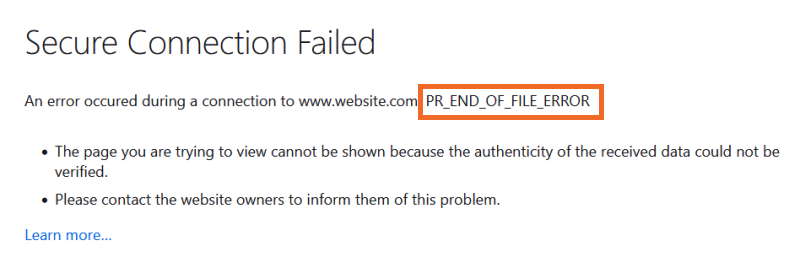
Austin B.How to fix PR_END_OF_FILE_ERROR (SSL) in Firefox
Mozilla Firefox users encounter the PR_END_OF_FILE_ERROR (Secure Connection Failed) in the default error message when they have attempted to visit a website and the browser was unable to establish a secure connection. This is because all cipher suites failed and when this happens, users encounter the same error message with any other website they then try to visit. The good news is this is not an error that happens often, the bad news is it will require your immediate attention.
We have 5 different fixes you can try:
- Uninstalling third-party security suite
- Disabling your VPN or Proxy
- Resetting & refreshing Firefox SSL settings
- Disabling DNS over HTTPS
- Create a new Firefox profile
Safari and Chromium browsers
If you are using Safari or chromium browser, then this will not be an error code that you will see. It’s an issue that only occurs through Firefox and there is more than one way to solve it that does not require deep technical knowledge. Before you start engaging another support party to get this solved for you, it’s not as complicated as you think. There are five different ways you can tackle this problem and when you encounter it if you’re not sure what is at the root cause, you may have to apply any or all of them.
Third-party software: Windows vs Mac and Linux
It’s not just different root causes and methods to solve the issue, the OS you are using will also have an impact on the way to resolve this. There is a marked difference between Mac and Windows and that relates to the third-party security software. Mac and Linux machines have internal infrastructures that enable safe browsing without additional anti-virus software so the first fix is aimed at Windows users.
1. Uninstalling third-party security suite
It’s been reported that certain security tools such as Bitdefender, REVE, and ESET can be a little overprotective and these security tools will insist on intercepting connection certificates and sending their own. With most websites, this is not an issue, but some might end up triggering the PR error code as a security precaution. The fix is to disable this protection or uninstall the security suite. This process will be different depending on the third-party security you are using but, in most cases, you should be able to do this directly from the taskbar icon of your antivirus or firewall suite.
Windows users
Individuals using Firefox on a Windows machine may have a situation where the security interprets cipher suites as a potential threat. In the first instance, you will need to:
- Locate the dashboard for your antivirus software and toggle it off.
- Once you have done this you can exit the program, and shut down your machine.
- Wait for around a minute before restarting. This is necessary to allow the computer memory time to clear.
- Once you restart, ensure that the software isn’t running on your desktop.
- You can then check your browser and if the error has cleared, you can resume browsing.
What if the error message persists?
If you’re still seeing the error message, you may need to look at your VPN or proxy settings because these can also impact your browser. A proxy works with a single app or site and a VPN secures your network traffic hiding your IP address when you visit websites and replacing it with the VPN provider’s IP address. Whilst both tools help to protect your identity and privacy, only a VPN will encrypt your data.
2. Disabling your VPN or Proxy
In the same way as the prior fix, your proxy or VPN settings may connect and cause your browser to think cipher suites don’t exist.
- Once again you will need to go to the settings of your VPN to disable it in just one click.
- As with the last fix reboot your machine and check your browser.
To disable proxy
If disabling the VPN has not worked then you’ll need to look at the proxy which is a more complex process but by taking a few more steps it is achievable.
Mac users
Step #1: Click on your Apple icon to open the system preferences followed by the network.
Step #2: Find the network icon and click
Step #3: Locate the network you are using which is usually Wi-Fi then click on the advanced tab
Step #4 In the Select a protocol to configure box, you will need to uncheck all boxes and click OK On the Next screen open proxies tap. Uncheck. Restart your Mac and check your browser.
Windows users
Disabling the proxy for Windows users is also straightforward.
- The first step is to type proxy into the search bar.
- Then open the shortcut of the proxy settings.
- Scroll to the manual proxy subsection. You will need to toggle the switch to off.
- Once again reboot your computer and attempt to navigate to a page. If the error persists you may need to look at your browser settings.
3. Resetting & refreshing Firefox SSL settings
Often users encountering this error code report that they have previously played around with SSL settings. To carry out this fix, you will need to head to the hamburger menu in Firefox also known as the three-bar menu.
Step #1 Look at the upper right corner with Firefox open and just underneath the closing X, you will see the hamburger icon.
Step #2 Once you have opened this menu, from the drop-down list select options click help then select more troubleshooting information.
Step #3 Next click on Refresh Firefox and again in the confirmation window.
Step #4 Once done, you will see a window with your imported information, click Finish and Firefox should open.
Step #5 Decide if you want Firefox to restore some of your windows and click let’s go!
Your SSL settings will be reset and at this point, you can check to see if you can browse.
If this hasn’t worked there is another option, you can try.
4. Disabling DNS over HTTPS
The DNS or domain name system is the naming system that essentially converts domain names into IP addresses which browsers then use to load the pages. DNS over HTTPS is a protocol that allows you to encrypt your connection to protect it from attacks and privacy intrusion.
Whilst this is a useful and helpful protocol, it can also be the cause of the PR and default error code. Once again as with prior fixes, you will need to disable it by heading to your Firefox preferences screen. You can access this through the hamburger menu in the browser.
- On the general screen, click the settings button that will open the connection settings.
- Once there, you will need to find the enable DNS over HTTPS option.
- Uncheck this box.
- Restart Firefox and see whether the error has disappeared.
5. Create a new Firefox profile
If you have worked through all the fixes we have suggested, and the error persists, it may be time to create a new Firefox profile. Before you gasp with horror over lost bookmarks, there is no need to panic, you can export or bookmark pages safely ready to import your new profile. You won’t want to lose your bookmarked library so there are numerous ways you can access this.
- You can click the toolbar to show bookmarks or try a keyboard shortcut
- Click export bookmarks to HTML and save this file.
You can now manage your Firefox profile by typing about profiles into the browser or bar and then clicking enter.
- The screen should display your current profiles and give you the option to create a new profile. Click this and enter a new username.
- Click confirm at the bottom of the profile.
You can then launch this new profile and should not encounter the error code. This is the final recommended fix after you have explored all others – see below for an explanation as to why this is the last action you should take.
FAQS
What causes PR_END_OF_FILE_ERROR in Firefox
- Third-party security
Whilst it is their job to protect, there are some slightly overzealous third-party suites. The issue arises when they intercept connection certificates and then send their own. - VPN or proxy interference
VPN or proxy software Acts as a go-between or middleman by intercepting a connection which can trigger this error message. - Unsupported or incorrect cipher variance
If you have modified your SSL settings this may mean your browser is now forcing the site for a variance that either Firefox or the website, you’re trying to access card support. - Firefox corrupted
Sometimes a corrupted profile can be the culprit for this error code. This may mean starting again with a new profile
Will this error happen again, or can I prevent it?
If you have carried out the fixes we have recommended, you should not have this error message again BUT be aware if you switch anti-virus software, there is a chance that it will intercept connections and trigger the error again. In which case, work through the steps in our first fix. The other way to prevent this from happening again is to not play around with the SSL settings.
Is PR_END_OF_FILE_ERROR indicative of other issues?
No, but it often occurs repeatedly because the user has not determined the root cause. It can be too easy to jump straight to setting up a new profile without interrogating other possible causes. Therefore, a new profile is a final fix when you have exhausted all other fixes.
Does this mean Firefox is not as good as other browsers?
Absolutely not! There are many positives to using the Firefox browser such as its privacy protection and cross-platform sync. The range of extensions and plugins you can use which Firefox make it incredibly flexible for designers or agencies
Is the security of my website causing PR_END_OF_FILE_ERROR for visitors?
Yes possible. When someone visits your website and sees this error message, or the “Not Secure” means they have been given a warning that your web page or website is not providing an encrypted connection. This will trigger protection software or for Firefox browsers the PR_END_OF_FILE_ERROR message.
What happens if a website is not secure?
The bottom line is not secure websites are vulnerable to cyber threats such as malware and cyberattacks. In the unfortunate event that your site falls victim to a cyberattack, it can impact the functionality of the site. From a business point of view, it can prevent visitors from accessing it, or even worse compromise your customers' personal information.
How do I choose a secure web hosting company?
With so many companies out there hosting, it can be hard to know which can help your business. Our ultra-secure hosting includes PCI-compliant hosting, malware scanning, 1 Tbps+ DDoS protection, web application firewall, brute force login protection, FTP security lock and 2FA as part of the package.
Why is web hosting security important?
We know that malware and cyber-attacks impact the functionality of your website. If you are selling a service and visitors can’t access your site, then they will go to a competitor. If you are selling a product and have an e-commerce site, then a cyber threat can mean customers can’t buy or worse have their personal information compromised. This impacts your business and bottom line.
 Reudiger Dalchow
Reudiger DalchowHow do I activate my free SSL?
Every 20i hosting package comes with a free wildcard SSL certificate, enabling you to use the more secure HTTPS protocol to keep your site users secure.
To activate the SSL, you’ll need to make sure you’ve pointed the domain name to our nameservers (why our nameservers are required).
These are:
- ns1.stackdns.com
- ns2.stackdns.com
- ns3.stackdns.com
- ns4.stackdns.com
With that done, you need to:
- Go to Manage Hosting.
- Select Options > Manage on the hosting package which you wish to activate the SSL.
- Under Security, click on the SSL/TLS icon.
- You will then see your domain name and an option to Activate Free SSL next to it - select this and the SSL will be applied to your domain.
- If you’d like all your visitors to use SSL connections (i.e. for HTTPS to always be used), simply select the Enable option at the bottom of the page.
Once the SSL Certificate has been activated, it will take up to 30 minutes to secure your website. This is due to the changes needed to be made on our load balancers.
 Lloyd Cobb
Lloyd CobbMy website shows as insecure due to mixed content?
Please note that if you have recently activated a 20i SSL certifcate for your domain, it can take up to 30 minutes to be installed across our load balancers.
After an SSL has been installed, the website still loads with an insecure warning
If the website is now showing your certificate but still has an insecure warning, this is often caused by 'mixed content' on the website. This means there is content on the page that is being loaded through a 'http://' URL. For a webpage to be classed as secure, all content must be loaded over HTTPS. This includes external images, JavaScript and CSS. You should search the source code of your website to locate the 'http://' references and update or remove them.
Finding Mixed Content
When visiting an HTTPS page in Google Chrome, the browser alerts you to mixed content as errors and warnings in the JavaScript console. You can open the console either from the View menu: View -> Developer -> JavaScript Console, or by right-clicking the page, selecting 'Inspect Element', then selecting 'Console'. You need to remove or update the 'http://' URLs listed in these errors and warnings in your sites source.
If your site is hosted on our Web Hosting you can also use ‘Why No Padlock?’ to identify mixed content: https://www.whynopadlock.com/
If the site is running WordPress, you can use the SSL Insecure Content Fixer plugin that should identify all mixed content and replace it with a secure version for you. You can find the plugin here: https://en-gb.wordpress.org/plugins/ssl-insecure-content-fixer/
Once all references on your website are called using https:// URLs, your site will load securely in your browser.
If your website is built using WordPress, please see here for more information on how to fix mixed content in WordPress.
 Lloyd Cobb
Lloyd CobbWhat are the differences between your SSL Certificates?
We offer 4 different types of SSL Certificate: Free, Simple, Wildcard and Extended. All 4 will give your website URL the 'https' prefix, showing that traffic is encrypted.
Let's Encrypt: Free Wildcard SSL Certificate
Our Free Secure Sockets Layer (SSL*) certificates are from Let’s Encrypt. These require you to use our nameservers. They help improve Google ranking and reassure potential customers that a site is secure. These are 'wildcard' certificates, which mean that they can cover subdomains of your website, such as subdomain.yoursite.com.
GeoTrust: Simple SSL Certificate
An ecommerce business might prefer to buy one of our Simple SSL certificates from GeoTrust, which doesn’t require you to use our nameservers. Both types include domain validation, which means that the certificate authority has checked the domain owner.
GeoTrust: Rapid SSL Wildcard Certificate
The Wildcard SSL certificate from GeoTrust will cover all subdomains of your website, whilst providing a $10,000 warranty which offers financial protection in the event of a security breach due to a flaw or error in the SSL certificate resulting in data loss.
GeoTrust: Extended SSL Certificate
Extended SSL is the highest class of SSL available. It includes more stringent checks on the company by the certificate authorities. Extended SSL lends more credibility to a website compared to a Free or Simple SSL. It includes a warranty and an Extended Validation certificate.
More information
For more information on our certificates for resellers, please see Reseller SSLs.
If you need to find out more about the verification process, please see What happens next after you've ordered an SSL certificate.
For Resellers a Simple SSL is £34.99, a Wildcard SSL is £99.99 and an Extended SSL is £234.99.
ℹ️ Click here to log in to My20i and purchase your SSL Certificate(s).
SSL and TLS: Certificates that secure website traffic have traditionally been called Secure Socket Layer Certificates. However, the SSL protocol has been superceded by the Transport Layer Security (TLS) protocol. All of our certificates use the TLS protocol, version 1.3. We use the term 'SSL Certificate' because more people are familiar with it.
 Lloyd Cobb
Lloyd CobbI`ve ordered a Simple or Extended SSL Certificate - what happens next?
All purchased SSL certificates - Simple and Extended SSLs - require email verification before being issued. What this means is an e-mail will be sent to admin@domain (where 'domain' is the domain you've purchased the certificate for, excluding "www.").
If you've ordered before setting this mailbox up - don't worry - just set up a forwarder or email account now and contact our support team who can resend the approval email for you.
If you've bought an Extended SSL, the nature of these certificates requires a higher level of vetting than any other certiifcate. As a result, our chosen certificate authority, Geotrust, will contact you by email within 24 hours with further instructions.
Our Free SSL certificates are verified through our nameservers: just order one through My20i and it will be added to your site in seconds. There is no verification process that you need to go through, unlike the purchased certificates.
To find out more about SSLs, please see What are the differences between our 3 types of SSL certs?
 Lloyd Cobb
Lloyd CobbWhy am I unable to activate the free SSL?
Every 20i hosting package includes a free wildcard SSL certificate.
To utilise the free SSL certificate, the domain name must use our nameservers (read here to find out why our nameservers are required).
These are:
- ns1.stackdns.com
- ns2.stackdns.com
- ns3.stackdns.com
- ns4.stackdns.com
If the Activate Free SSL button does not show within the SSL/TLS section, under the Security header or you get an error message upon attempting to click the Activate Free SSL button, please check the following:
Does the domain name have DNSSEC enabled?
DNSSEC can block the platform from verifying the domain name is using 20i’s nameservers.
This can be checked from a Whois lookup. If DNSSEC is Signed, this will need to be disabled at your domain registrar.
Nameserver propagation
If you have recently changed your nameservers to 20i’s, there is often a propagation delay until the domain name switches from the previous nameservers to 20i’s.
It can take up to 48 hours for nameserver changes to propagate across the web, but in most cases, it will be completed much faster.
20i utilises Google’s Public DNS and so you can flush the DNS cache to clear the resolvers.
Does the domain name have any ‘acme-challenge’ CNAME records within the DNS zone?
Acme-challenge CNAME records are used to validate Let’s Encrypt SSL certificates.
Due to the 20i free wildcard SSL certificates being issues from Let’s Encrypt, this can block the platform from issuing the SSL certificate.
The acme-challenge CNAME records look like this: _acme-challenge.example-domain.com. Once the DNS record has been removed, and the DNS propagated, the Activate Free SSL button should appear.
Nameserver sub-delegation
Sub-delegation of Nameservers is where the nameservers are pointing to 20i (StackDNS) through another provider but at the registry the nameservers are pointing to another provider.
This is actioned by the 20i nameservers being added as a NS record in the DNS rather than a nameserver. If this is the case, please contact your domain provider.
 Jordan Graves
Jordan GravesWhat is a CAA record?
CAA (Certificate Authority Authorization) records are DNS (Domain Name System) resource records that specify which certificate authorities (CAs) are authorized to issue SSL/TLS (Secure Sockets Layer/Transport Layer Security) certificates for a specific domain. These records help domain owners maintain control over the issuance of SSL/TLS certificates for their domains and enhance security by preventing unauthorized CAs from issuing certificates.
How can I add a CAA record at 20i?
To add a CAA record, you'll need to:
- Head to Manage Hosting
- Select the package name
- Select Options
- Select Manage
- Go to Manage DNS under Domain Names
Here's how CAA records work:
Domain Owner's Control: When you own a domain and want to control which CAs can issue SSL/TLS certificates for that domain, you can create CAA records in your domain's DNS settings.
CAA Record Format: A CAA record typically consists of the following components:
- Flag: A flag that specifies the meaning of the record.
- Tag: A tag that indicates the property or issue for which the record is being created.
- Value: The value associated with the tag, which specifies the CA(s) that are authorized to issue certificates for the domain.
Flag Values:
- "0" indicates that the CA specified in the CAA record is the only one authorized to issue certificates.
- "128" indicates that the CA specified in the CAA record is authorized, but other CAs are not prevented from issuing certificates.
Tag Values:
- "issue" is the most commonly used tag, which specifies the CAs that are allowed to issue certificates for the domain.
- Other tags, like "iodef" (for incident reporting) and "issuewild" (for wildcard certificates), can be used for specific purposes.
Here's an example of a CAA record:
example.com. CAA 0 issue "ca.example.net"
In this example:
- The domain is "example.com."
- The flag is set to "0," indicating that only the CA specified in the "issue" tag is authorized to issue certificates for the domain.
- The "issue" tag specifies "ca.example.net" as the authorized CA.
With this CAA record in place, only the CA "ca.example.net" is allowed to issue SSL/TLS certificates for "example.com." If another CA attempts to issue a certificate for this domain, it should check the CAA records and honor the restrictions specified in them.
CAA records are a useful security mechanism to prevent unauthorized certificate issuance and enhance the overall security of websites and online services. Domain owners can configure these records to specify their preferred CAs and minimize the risk of certificate-related security issues.
 Chris Wright
Chris Wright*.stackcp.com SSL certificate is showing instead of my domain's SSL
Sometimes, you may see when loading your website using https that it shows a warning that it’s trying to use the *.stackcp.com SSL certificate:
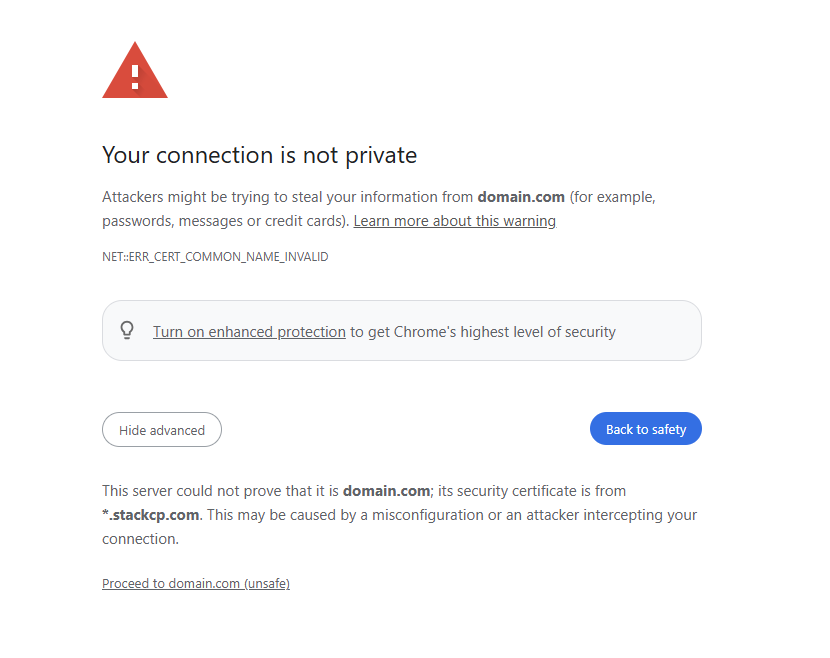
The main cause for this is usually due to an SSL not being installed. At 20i, we offer free SSL’s which you can install on your hosting package. You can follow this article to activate your free SSL.
We also sell SSL certificates, so you can purchase one for the hosting package within your account as well.
Another reason could be that the SSL is still being installed on the package. When any SSL is installed on the package, it will take around 30 minutes to be installed on our platform before it starts working. If you have installed the SSL recently, you may just need to allow more time for this to install.
If you see that an SSL has been installed on the hosting package and you have allowed at least 30 minutes for this to install, and you still see this error, get in touch with our support team, who can investigate further.
 Corey Seymour
Corey Seymour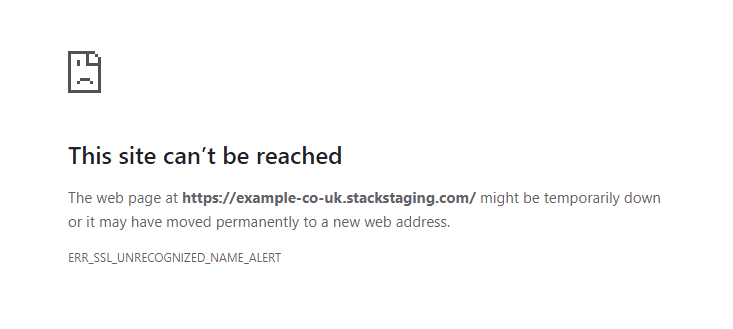

 Ben Gayson
Ben Gayson