Web Hosting – Website Problems Questions
Website problems: read support articles and find solutions to common issues you might experience when using 20i's web hosting.
Why is my website not able to send email?
A common reason for this relates to the address not matching your site domain.
To help improve email deliverability and help prevent spam being sent from our network, the 'Sender' address for your message must match the domain name of the website used to send the message.
If this header is set to a domain not assigned to your hosting package, the message will not be sent.
Websites will also be unable to send mail if there is malware found on the site. If malware is found it will need to be removed and another malware scan run before the website will be able to send mail again. More information on malware scanning can be found here.
If you have any further issues please contact our Support Team.
 Lloyd Cobb
Lloyd CobbCan I add SPF records for my domain name?
Sender Policy Framework (SPF) records help reduce the chance of your domain being spoofed in spam messages. It can also increase the deliverability of e-mail to external providers such as Gmail and Outlook.
We maintain an SPF record that is kept up to date with all IP addresses used to transmit email from our network. This ensures that any email sent from our services passes an SPF check. To use this on your domain, you need to add a TXT record in DNS.
How to add SPF records automatically
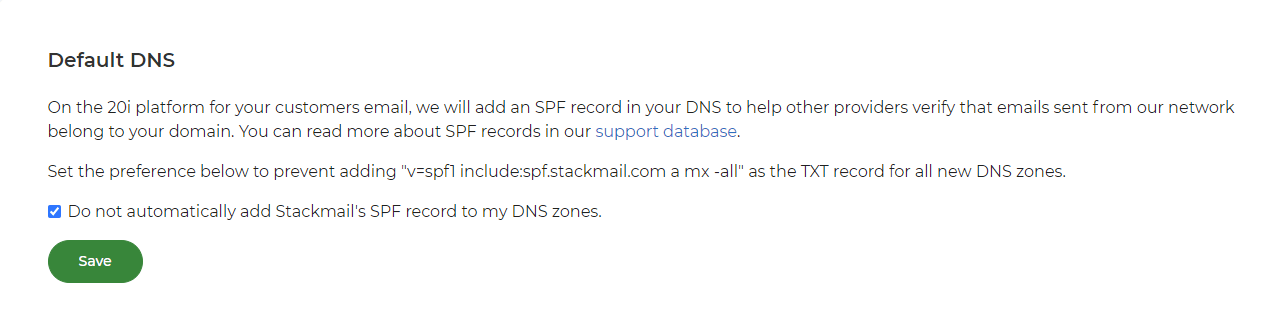
By default, all newly provisioned hosting packages will have an SPF record for Stackmail added automatically. If you don't want this to happen, then you can opt-out by following the steps below:
- Go to Account Preferences in My20i.
- Select Do not automatically add Stackmail's SPF record to my DNS zones and click Save.
How to add SPF records manually
Firstly, access the DNS Management interface for your domain name. If the domain is registered with us, you can access this from the Manage Domains area of the control panel.
If the domain is not with us but is assigned to a hosting package, you can reach this interface via the Manage Hosting -> Select Package -> Manage DNS section.
Towards the bottom of the Manage DNS page, you will see 3 inputs to allow you to add new records. To add it:
- Leave the Name field blank
- Select TXT for Type
- Enter v=spf1 include:spf.stackmail.com a mx -all as data

Then save the changes. Your domain is now protected by an SPF record.
You can use the same record for all domains that use our mail services, however it should be noted that the above record will tell external providers all of your e-mail should originate from our network. If this isn't the case the record should be updated accordingly.
 Lloyd Cobb
Lloyd CobbHow do I use traceroute (tracert)?
Traceroute, or tracet, is a tool used for diagnosing network-related issues. It does this by displaying the route to the destination specified - a domain name or an IP address - and records how long it takes packets to reach that destination. Occasionally your Web Hosting Provider may ask you to perform a traceroute.
How to use traceroute?
Here's how to run tracet on the 3 most common OS:
Windows
- Click 'Start'
- Type in Run and then click on the icon that appears (a box should open)
- Type cmd and then press OK to open command prompt.
- In the window that appears, type in: tracert yourdomain.com (or the IP address depending on the issue) and then press 'Enter'.
macOS
- Browse to Applications -> Utilities -> Terminal
- Then type traceroute followed by a space and then a website or IP address you need to diagnose, i.e. traceroute yourdomain.com then press 'Enter'.
Linux
- Open a Terminal window
- Type: traceroute yourdomain.com (or replace 'yourdomain.com' with an IP address if requested to do so)
 Lloyd Cobb
Lloyd CobbHow do I check 20i server status?
You or your customers can check the status of the 20i platform on the Stack Status page: https://www.stackstatus.com/.
Stack Status is a 'white label' page that doesn't include any links to 20i. If we're carrying-out maintenance, this is where you can receive progress updates.
In the unlikely event we experience any issues, this is where status messages will be published.
What do I do if I believe a site is in breach of 20i's policies?
20i imposes a strict Acceptable Use Policy and Terms of Service which customers must adhere to. These cover illegal activities, prohibit certain content hosted through us and includes a zero-tolerance spam policy.
A 20i customer breaking these terms and conditions could have our services withdrawn from them, and potentially be reported to the authorities for illegal activity.
If you suspect any 20i customer of abusing our rules, you should report to them to us.
We recommend to email us at abuse@20i.com in the first instance.
 Chris Wright
Chris Wright403 Response on POST Request
As part of our Web Application Firewall we occasionally filter invalid POST requests when we detect malicious traffic towards our network.
This shouldn't cause any problems with software that is using standard HTTP POST requests to reach your website. However, if you've written a custom application you will need to ensure the code making the POST is setting the appropriate Content-Length header in the request.
curl/libcurl will do this by default if you send any HTTP POST data. But if your custom code is simply overriding the HTTP method to POST without setting/sending any data, this header may be missing and result in the block.
You can easily resolve this by setting this header manually, for example:
curl_setopt($ch, CURLOPT_HTTPHEADER, array('Content-Length: ' . strlen($fields)));
However, it may be easier to simply use the built-in POST fields which automatically populate this header as required.
curl_setopt($ch, CURLOPT_POSTFIELDS, $fields);
 Austin B.
Austin B.How do I fix a 4XX error?
4XX errors cover a range of HTML errors that usually occur when a file that is attempting to be accessed cannot be found, has incorrect permissions or is inaccessible by the person loading it.
The causes can range from a simple typo in the URL to security rules restricting users from entering certain areas. Identifying the specific type of 4XX error can help you to understand the cause, who is impacted, and how to fix the error.
Types of 4XX Error
4XX errors have four main types that are commonly encountered, each with their own sub-header that explains what the specific problem is – these can be as follows:
Below, we’ll break down each error and some of the most common causes so you can get your site or page back online and working again as quickly as possible.
400 Bad Request
400 Bad Request errors are usually caused by the request that has been sent to the server either being corrupt or in a format that the server cannot recognise. This can be down to either the data that the browser is sending to the site, or something on the site corrupting the data.
If you’re experiencing this error, you’ll first want to try clearing your browser’s cookies and cache, as the browser may be trying to use an invalid or expired cookie to navigate and log into the site. This then results in the server responding that it does not understand the request. The cookie that your browser has cached may also be corrupt, which could lead to the same result.
If the issue persists after clearing your cache and cookies, it may be something on the website itself. It’s worth disabling any non-critical site plugins or extensions to rule these out, and note any recent changes made prior to the 400 errors cropping up. If the changes were substantial, it may be worth restoring to a backup of the site prior to these changes to see if this reverts the error.
401 Unauthorized
401 Unauthorized occurs when you try to access an area of a site that is being protected by either password encryption or a security rule. Usually, you’ll experience this error if you either try to access an area without providing the necessary login information, or our server’s security blocks the request.
Most commonly, this is due to a site being protected by password requirements set within a .htaccess and .htpasswd file combination. These state that a folder of a site is protected by a specific username and password combination, and any requests made to the site that lack these details will be denied. If you’re experiencing this error, check your site’s .htaccess files to ensure that there’s no set security rules or password protection that could be blocking the request.
Alternatively, the requests could be hitting our StackProtect bot protection. This tool actively filters your site against potentially harmful or suspicious requests, providing a 401 for any request that fails the checks it runs.
However, sometimes these connections can be filtered incorrectly, which is known as a false positive. In cases where your site request is being filtered by StackProtect, you’ll see a message prior to the 401 error stating that the connection is being checked. If this is the case, you should reach out to our Support Team, who can look to get the connection checked and see if we can prevent this being filtered on a case-by-case basis.
403 Forbidden
A 403 Forbidden error indicates that user trying to access the site does not have the necessary permissions to do so. This can be due to security policies set by the site itself, either through plugins or rules in a .htaccess file, or it can be because the permissions of the site files aren’t set correctly.
If you’re experiencing a 403 error consistently when visiting a website, check the site to make sure that there aren’t any security plugins or addons that could be blocking access to your browser or IP. Also ensure that your site’s .htaccess file doesn’t have any rules that deny access to specific IPs or types of file. If you do, you’ll need to disable or remove these to get the site to be accessible again.
If there aren’t any problems with security rules, then the 403 is most likely being caused by incorrectly set file permissions. File permissions define who can and cannot access certain files, and what services can be used to access them. We have an inbuilt File Permissions Checker that can be used to scan and fix incorrectly-set permissions.
The File Permission Checker is available for all hosting packages via the My20i control panel.
To access this tool:
- Log into My20i and head to your Manage Hosting area
- Select Options > Manage on the hosting package you’d wish to edit
- Head to the Web Files section and select File Permissions Checker
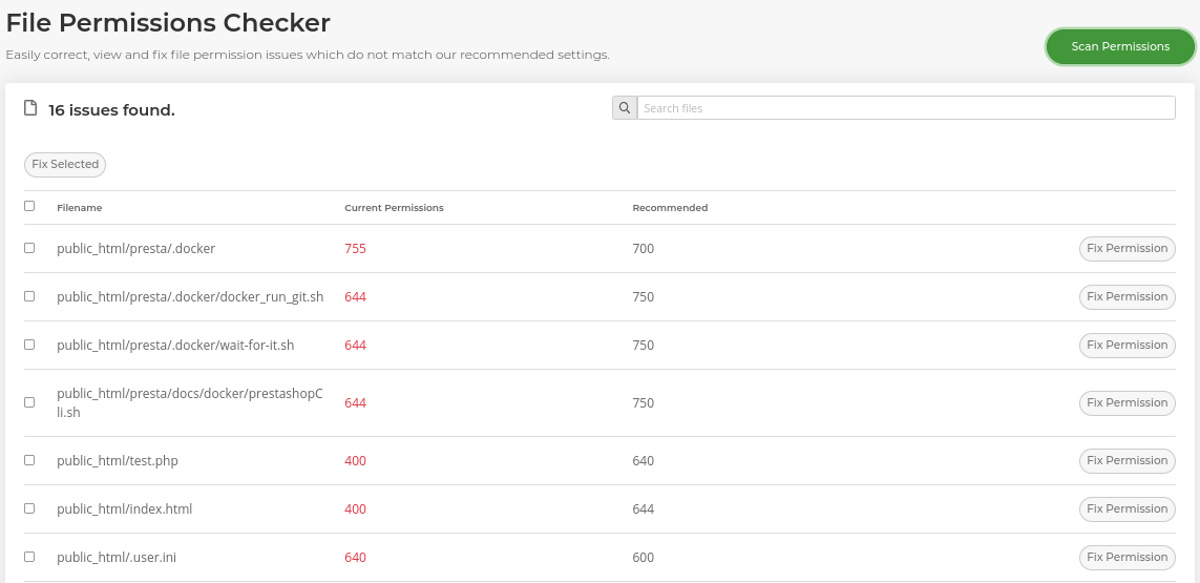
Select Scan File Permissions
Once the scan finishes, check the boxes of any files that are detected to have the wrong permissions, and select Fix Selected to resolve the error.
404 Not Found
A 404 Not Found error is caused by the requested page, file or site not being locatable by the server. Usually this is due to the file or page simply not existing on the server itself, or it’s under a different name than the given query. This can often be down to a typo in the URL, which results in the incorrect page or file to be searched for. If you’re experiencing this on your site, it’s worth double-checking to make sure you haven’t made any mistakes when trying to access the page in question.
If it’s not the case, it’s worth checking to see if the requested file does exist on your site. Check your site files: if the file simply isn’t there, you’ll need to upload a copy of the missing file in order to allow it to be accessible once more. Certain Content Management Systems (CMS) such as WordPress use permalinks instead of files per page. These are URLs generated by the site that display a post or page live, rather than storing it locally as a standalone file or folder. If a page within a WordPress site is throwing a 404 but your main site page isn’t, there may be a problem with the generated permalinks, and you’ll need to regenerate them to fix the error.
To do so:
- Sign into wp-admin on your site and head to Settings > Permalinks.
- In the main permalinks area, make sure that the correct value for the URLs is set, and then hit Save Changes. This will force WordPress to fully regenerate the permalink structure and should bring the pages back online once more.
As you can see, 4XX errors come in a wide variety of types and forms, and fixing them can depend on the specific error. If you’re encountering these types of error on your site, it’s worth noting down the specific error code and how you’re accessing the site to get the error. Doing so can help you narrow down and isolate the cause, so you can get your site back online as swiftly as possible.
 Reudiger Dalchow
Reudiger DalchowWhat is a 429 error?
A 429 error, also known as Too Many Requests error, is an HTTP status code that is returned by a server to indicate that the user has sent too many requests in a given time frame and has exceeded the rate limits imposed by the server or an associated service. It is part of an abuse rule to protect against both brute force attackers and vulnerability scanners. It will only trigger when a single IP address has sent 'bad requests'. Requests such as 404 or 403 responses are identified as ‘bad requests’, 200 OK responses would not trigger the rule.
The purpose of the 429 error is to prevent abuse or overloading of a server or service by limiting the number of requests a single user or client can make within a specific time period. This is commonly used in APIs and web services to ensure fair usage and to protect the server from being overwhelmed by excessive traffic.
When you encounter a 429 error, you may need to wait until the rate-limiting period has passed or reduce the frequency of your requests to comply with the rate limits set by the server or service.
The root cause of the ‘bad requests’ can vary – However, one of the biggest causes are scripts in the background that are failing to load, these are normally in the 4xx range e.g. 403 and 404's, when you're making updates can you open console and check if anything is failing to load in. If you visit the site via a different connectin (i.e. mobile data), then it should work fine.
If you are experiencing a 429 error and need further assitance then please feel free to reach out to our support team for further assistance. Our team will need to know the steps to replicate the 429 error as well as the IP address of the device you're connecting from (https://ipinfo.io/ip).
 Chris Wright
Chris WrightHow do I clear my browser cache?
Web content is often cached locally on your device to improve loading times. However, there are times when it's necessary to clear your browser cache to ensure that recent changes on websites are visible. Whether you're a web developer or a regular user, knowing how to clear the cache in popular browsers is a valuable skill. In this guide, we'll walk you through the steps to clear the cache in some of the most widely used web browsers.
Clearing the Browser Cache:
Google Chrome:
Open Chrome: Launch Google Chrome on your computer.
Access Settings: Click on the three vertical dots (menu icon) in the upper-right corner to open the menu. From there, hover over "More tools," then select "Clear browsing data." Alternatively, click here.
Choose Data to Clear: In the "Clear browsing data" window, make sure "Cached images and files" is selected. You can also choose a time range to clear based on your preference.
Clear Data: Click the "Clear data" button to remove the cached files and images from your browser.
To directly access the Clear Browsing Data page, you can use the URL: chrome://settings/clearBrowserData
Mozilla Firefox:
Open Firefox: Launch Mozilla Firefox on your computer.
Access Options: Click on the three horizontal lines (menu icon) in the upper-right corner and select "Options."
Privacy & Security: In the left sidebar, click on "Privacy & Security." Alternatively, click here.
Clear Data: Scroll down to the "Cookies and Site Data" section and click the "Clear Data" button.
Choose Data to Clear: Make sure "Cached Web Content" is selected. You can also choose to clear cookies if desired.
Clear: Click the "Clear" button to remove the cached data.
To directly access the Clear Browsing Data page, you can use the URL: about:preferences#privacy
Microsoft Edge:
Open Edge: Launch Microsoft Edge on your computer.
Access Settings: Click on the three horizontal dots (menu icon) in the upper-right corner and select "Settings."
Privacy, Search, and Services: In the left sidebar, click on "Privacy, Search, and Services."
Clear Browsing Data: Under the "Clear browsing data" section, click on "Choose what to clear."
Choose Data to Clear: Ensure "Cached images and files" is selected. You can also choose a time range or clear other data like cookies if needed.
Clear: Click the "Clear" button to delete the selected data.
To directly access the Clear Browsing Data page, you can use the URL: edge://settings/clearBrowserData
Safari (macOS):
Open Safari: Launch Safari on your Mac.
Access Preferences: Click on "Safari" in the menu bar and select "Preferences."
Privacy Tab: Go to the "Privacy" tab.
Manage Website Data: Click on the "Manage Website Data" button.
Clear Cache: In the window that appears, click "Remove All" to clear all cached data or select specific websites and click "Remove" for individual site data.
Confirm: Confirm the action when prompted.
Safari (iOS):
Open Settings: On your iPhone or iPad, open the "Settings" app.
Safari Settings: Scroll down and tap on "Safari."
Clear History and Website Data: Under the "Privacy & Security" section, tap on "Clear History and Website Data."
Confirm: Confirm the action when prompted.
Clearing your browser cache can help resolve issues like loading errors, outdated content, and privacy concerns. Use this guide when necessary to ensure you experience a smoother and more up-to-date web.
 Chris Wright
Chris WrightWhat should I do if my website becomes malware infected?
If you believe that your site may have been hacked, or if you have been alerted to the presence of malware through our Malware Scanner, you can follow this guide to restore your site and then protect it from further damage.
Please note: Our support team are unable to perform direct malware removal or provide extensive support with such operations, however, you can use the steps below as a guide on restoring your site to full working functionality.
Restore From Backup
By far the easiest and most efficient way of resolving a malware infection is by restoring from a known-good backup. With our Timeline Backups service, you can easily restore the website files and database from a previous date within the last 30 days.
You’ll want to perform a full restore as opposed to a partial one in order to ensure that all infected files are fully removed and that none remain.
Redownloading WordPress Core Files
If your website is built using WordPress, then you can use their easy way of redownloading the core files via the WP CLI tool.
To use the tool, you’ll first need to setup an SSH connection to your package.
Once connected, you can run the below commands to find your current version of WordPress and then redownload its core files.
1. Check the current WordPress version:
wp core version
You’ll then want to place the appropriate version number into the command below. In this case we’re using 6.3.2
2. Re-download the core files:
wp core download –version=6.3.2 --skip-content --force
You can confirm the validity and integrity of the WordPress core files using the following command:
wp core verify-checksums
If you’re using a WordPress package type, you can also use the Checksum Report tool under the WordPress Tools section to verify the checksums of the core files.
Securing The Site
Once you’ve restored the site to a working condition, you’ll want to secure it against further infections. The below suggestions can help prevent further issues:
- Ensure that regular backups are being taken using a service such as Timeline Backups
- Keep WordPress and all plugins and themes up to date
- Install and utilise a security plugin such as WordFence
- Disable and remove unused plugins and themes, as these are an easy target for hiding malicious code
- Reset the password for the site’s database and for all admin users
- Ensure that admin access is only given to those who really need it, and enforce more restricted access to all other users
Contact A Security Professional
If you’re unable to fully remove the malware infection or believe your site may still be at risk, we would recommend getting in touch with a security professional who should be able to provide a more in-depth analysis of the site, along with remediation steps.
Whitelist Request
If you believe a file is being incorrectly marked as malware by our Malware Scanner, please contact our support team. We'll be able to pass the file to our security team who can audit the file and consider whitelisting it if necessary. Please note that we cannot guarantee a file will be whitelisted.
 Joshua Rosato
Joshua RosatoWhat is a 401 Error?
The HTTP 401 error, also known as "Unauthorized," is a status code that informs the client that the request lacks valid authentication credentials or the provided credentials are insufficient to access the requested resource. When a client receives a 401 error, it means that the server requires authentication before granting access to the resource, and the client hasn't provided the necessary credentials.
Now, let's explore the two primary causes of HTTP 401 error: StackProtect and HTTP authentication.
StackProtect: Protecting Against Bots
StackProtect is part of our security software and operates similarly to popular services like Cloudflare. Its primary function is to safeguard websites and online services from automated bots and unauthorized access. One of the techniques StackProtect employs is presenting users with a CAPTCHA challenge.
When StackProtect detects suspicious activity, such as “bot-like” behaviour or access attempts from a known-bad IP address or user-agent, it can trigger a CAPTCHA challenge for the client. The CAPTCHA is a test designed to differentiate between human users and automated bots. If the user fails to pass this test, the server may return an HTTP 401 error. In this scenario, the client must prove its human identity by successfully completing the CAPTCHA to gain access.
HTTP Auth: Protecting Against Invalid User Credentials
HTTP authentication is a mechanism for clients to provide valid credentials to access protected resources on a server. There are different methods of HTTP authentication, such as Basic Authentication, Digest Authentication, and Bearer Token Authentication. The server relies on these credentials to verify the client's identity and determine whether access should be granted.
The most common cause of an HTTP 401 error in the context of HTTP auth is when the client provides incorrect or missing authentication credentials. This could be due to a typo in the username or password, or the client failing to include the required authentication headers in the request.
Another cause of an HTTP 401 error in the context of HTTP auth is expired credentials. Authentication credentials often have a limited validity period. If the client uses expired credentials, the server will respond with a 401 error, signalling the need to reauthenticate and obtain fresh credentials.
Resolving HTTP 401 Errors
If users are continuously seeing the StackProtect page or if a particular bot is being blocked from accessing the site, please raise a support ticket and our support team can provide further advise on whitelisting access or disabling StackProtect for the package.
If users are failing to authenticate against the site, then you should ensure that the login credentials being used are correct. HTTP authentication is commonly setup using the .htaccess and .htpasswd files, so these can be checked to change or disable the authentication mechanism.
Our support team are happy to help with the process of finding where the authentication prompt may be coming from.
 Joshua Rosato
Joshua RosatoAllowed PHP Memory Size Exhausted
What does 'PHP Memory Size Exhausted' error look like?
One common cause for a site to experience a 500 error is due to the site exhausting all of its allocated PHP memory.
 Understanding the Error Message
Understanding the Error Message
The error message shown above indicates that a script on the site has used up all available PHP memory. This means there is no remaining memory for the site to carry out further operations, resulting in the 500 error.
Diagnosing PHP Memory Issues
If your site is down, checking your package error logs can help determine if it's a PHP memory issue. A message similar to the one in the image above will appear if there is a PHP memory problem.
Increasing PHP Memory Limit: A Guide
To resolve this issue, you may need to increase the PHP memory limit for your site. This adjustment can be made in the PHP Configuration section of your hosting package's control panel. A
lternatively, you can increase the PHP memory limit via your .user.ini file, especially if you're more comfortable making changes through SSH or FTP.
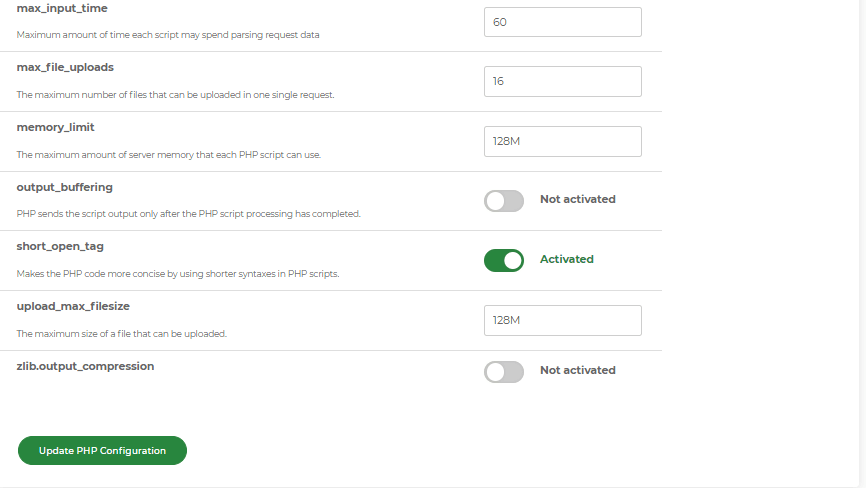
Standard and Recommended PHP Memory Limits
The standard PHP memory limit is set at 128M. Typically, doubling the value to 256M or 512M is sufficient. Although the maximum limit is 2048M, it's highly unusual for a site to require this amount. In most scenarios, 512M is ample for the site's needs.
 Ben Gayson
Ben Gayson